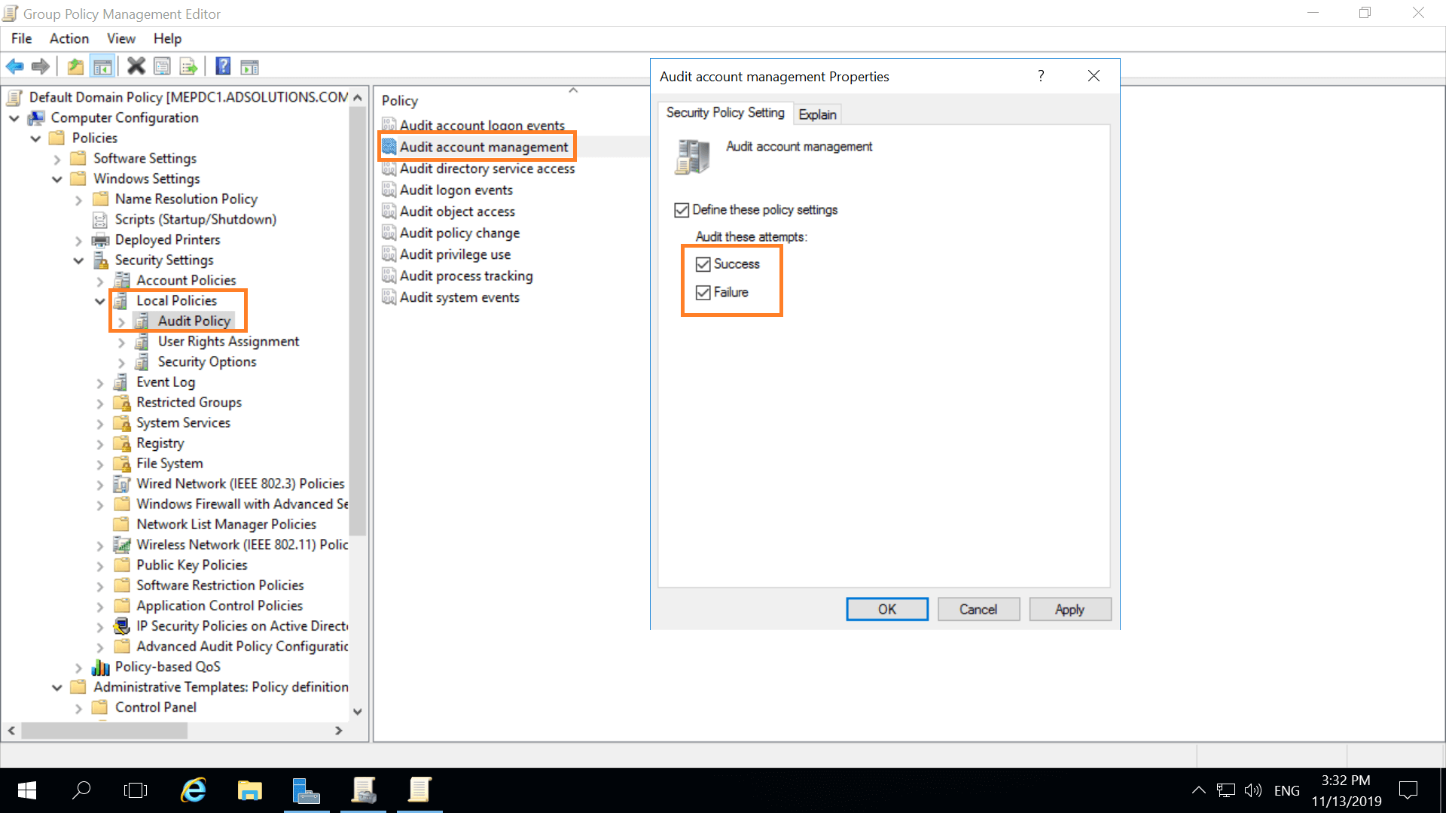
Windows Event Log Password Change . according to ultimate windows security you should look for the following events in the security event log: This event is logged both for. Logon id allows you to correlate. this event generates every time an account attempted to reset the password for another account. though there are several event ids that the microsoft windows security auditing source contains, the primary event ids that you should be. For user accounts, this event generates on domain. in this article, we will discuss the steps required to detect password changes and resets in active directory. Open event viewer and search security log for event id’s: attributes show some of the properties that were set at the time the account was changed. this event generates every time a user attempts to change his or her password.
from www.manageengine.com
according to ultimate windows security you should look for the following events in the security event log: Open event viewer and search security log for event id’s: this event generates every time a user attempts to change his or her password. For user accounts, this event generates on domain. Logon id allows you to correlate. in this article, we will discuss the steps required to detect password changes and resets in active directory. This event is logged both for. though there are several event ids that the microsoft windows security auditing source contains, the primary event ids that you should be. this event generates every time an account attempted to reset the password for another account. attributes show some of the properties that were set at the time the account was changed.
How to check password change history in Active Directory
Windows Event Log Password Change This event is logged both for. Open event viewer and search security log for event id’s: according to ultimate windows security you should look for the following events in the security event log: in this article, we will discuss the steps required to detect password changes and resets in active directory. this event generates every time an account attempted to reset the password for another account. though there are several event ids that the microsoft windows security auditing source contains, the primary event ids that you should be. This event is logged both for. For user accounts, this event generates on domain. attributes show some of the properties that were set at the time the account was changed. Logon id allows you to correlate. this event generates every time a user attempts to change his or her password.
From www.manageengine.com
Configure event log settings Windows server audit guide ADAudit Plus Windows Event Log Password Change attributes show some of the properties that were set at the time the account was changed. For user accounts, this event generates on domain. this event generates every time an account attempted to reset the password for another account. This event is logged both for. Open event viewer and search security log for event id’s: this event. Windows Event Log Password Change.
From www.beyondtrust.com
Important Windows Event IDs Which Events You Should… BeyondTrust Windows Event Log Password Change though there are several event ids that the microsoft windows security auditing source contains, the primary event ids that you should be. attributes show some of the properties that were set at the time the account was changed. in this article, we will discuss the steps required to detect password changes and resets in active directory. . Windows Event Log Password Change.
From www.anoopcnair.com
Various Critical Windows 11 Event ID List HTMD Blog Windows Event Log Password Change This event is logged both for. attributes show some of the properties that were set at the time the account was changed. Open event viewer and search security log for event id’s: this event generates every time an account attempted to reset the password for another account. according to ultimate windows security you should look for the. Windows Event Log Password Change.
From learn.microsoft.com
Introdução à LAPS do Windows e o Windows Server Active Directory Windows Event Log Password Change Logon id allows you to correlate. attributes show some of the properties that were set at the time the account was changed. though there are several event ids that the microsoft windows security auditing source contains, the primary event ids that you should be. For user accounts, this event generates on domain. this event generates every time. Windows Event Log Password Change.
From www.manageengine.com
Windows Event ID 4724 An attempt was made to reset an account's Windows Event Log Password Change this event generates every time an account attempted to reset the password for another account. For user accounts, this event generates on domain. Open event viewer and search security log for event id’s: in this article, we will discuss the steps required to detect password changes and resets in active directory. Logon id allows you to correlate. . Windows Event Log Password Change.
From blogs.manageengine.com
Monitoring service account password changes in Active Directory Windows Event Log Password Change according to ultimate windows security you should look for the following events in the security event log: For user accounts, this event generates on domain. this event generates every time an account attempted to reset the password for another account. in this article, we will discuss the steps required to detect password changes and resets in active. Windows Event Log Password Change.
From yadyn.blogspot.com
yadyn NETLOGON Event 3210 and Corrupted Domain Authentication Woes Windows Event Log Password Change this event generates every time an account attempted to reset the password for another account. this event generates every time a user attempts to change his or her password. in this article, we will discuss the steps required to detect password changes and resets in active directory. Logon id allows you to correlate. though there are. Windows Event Log Password Change.
From www.manageengine.com
How to check password change history in Active Directory Windows Event Log Password Change according to ultimate windows security you should look for the following events in the security event log: this event generates every time an account attempted to reset the password for another account. attributes show some of the properties that were set at the time the account was changed. though there are several event ids that the. Windows Event Log Password Change.
From newsitn.com
How to filter Security log events for signs of trouble News ITN Windows Event Log Password Change this event generates every time an account attempted to reset the password for another account. in this article, we will discuss the steps required to detect password changes and resets in active directory. this event generates every time a user attempts to change his or her password. attributes show some of the properties that were set. Windows Event Log Password Change.
From www.vrogue.co
Event Viewer Windows Logs Benisnous Extend Security Eventviewer Vrogue Windows Event Log Password Change For user accounts, this event generates on domain. this event generates every time a user attempts to change his or her password. though there are several event ids that the microsoft windows security auditing source contains, the primary event ids that you should be. Open event viewer and search security log for event id’s: This event is logged. Windows Event Log Password Change.
From www.windowscentral.com
How to use Event Viewer on Windows 10 Windows Central Windows Event Log Password Change attributes show some of the properties that were set at the time the account was changed. this event generates every time a user attempts to change his or her password. though there are several event ids that the microsoft windows security auditing source contains, the primary event ids that you should be. this event generates every. Windows Event Log Password Change.
From www.ultimatewindowssecurity.com
Windows Security Log Event ID 627 Change Password Attempt Windows Event Log Password Change in this article, we will discuss the steps required to detect password changes and resets in active directory. For user accounts, this event generates on domain. according to ultimate windows security you should look for the following events in the security event log: This event is logged both for. though there are several event ids that the. Windows Event Log Password Change.
From www.pinterest.com
Event ID 4625 How to Fix the Failed Logon Error in 2023 Event id Windows Event Log Password Change Open event viewer and search security log for event id’s: this event generates every time an account attempted to reset the password for another account. Logon id allows you to correlate. according to ultimate windows security you should look for the following events in the security event log: For user accounts, this event generates on domain. in. Windows Event Log Password Change.
From learn.microsoft.com
4723(S, F) An attempt was made to change an account's password Windows Event Log Password Change this event generates every time a user attempts to change his or her password. Open event viewer and search security log for event id’s: This event is logged both for. according to ultimate windows security you should look for the following events in the security event log: For user accounts, this event generates on domain. in this. Windows Event Log Password Change.
From windowsreport.com
Event ID 4738 A User Account was Changed [Fix] Windows Event Log Password Change though there are several event ids that the microsoft windows security auditing source contains, the primary event ids that you should be. in this article, we will discuss the steps required to detect password changes and resets in active directory. this event generates every time a user attempts to change his or her password. Logon id allows. Windows Event Log Password Change.
From www.windowscentral.com
How to use Event Viewer on Windows 10 Windows Central Windows Event Log Password Change in this article, we will discuss the steps required to detect password changes and resets in active directory. according to ultimate windows security you should look for the following events in the security event log: Logon id allows you to correlate. This event is logged both for. Open event viewer and search security log for event id’s: For. Windows Event Log Password Change.
From blog.lithnet.io
Getting started with Password Protection Part 1 Blocking Windows Event Log Password Change this event generates every time a user attempts to change his or her password. This event is logged both for. For user accounts, this event generates on domain. in this article, we will discuss the steps required to detect password changes and resets in active directory. though there are several event ids that the microsoft windows security. Windows Event Log Password Change.
From www.hackingarticles.in
Understating Guide of Windows Security Policies and Event Viewer Windows Event Log Password Change attributes show some of the properties that were set at the time the account was changed. This event is logged both for. in this article, we will discuss the steps required to detect password changes and resets in active directory. For user accounts, this event generates on domain. according to ultimate windows security you should look for. Windows Event Log Password Change.